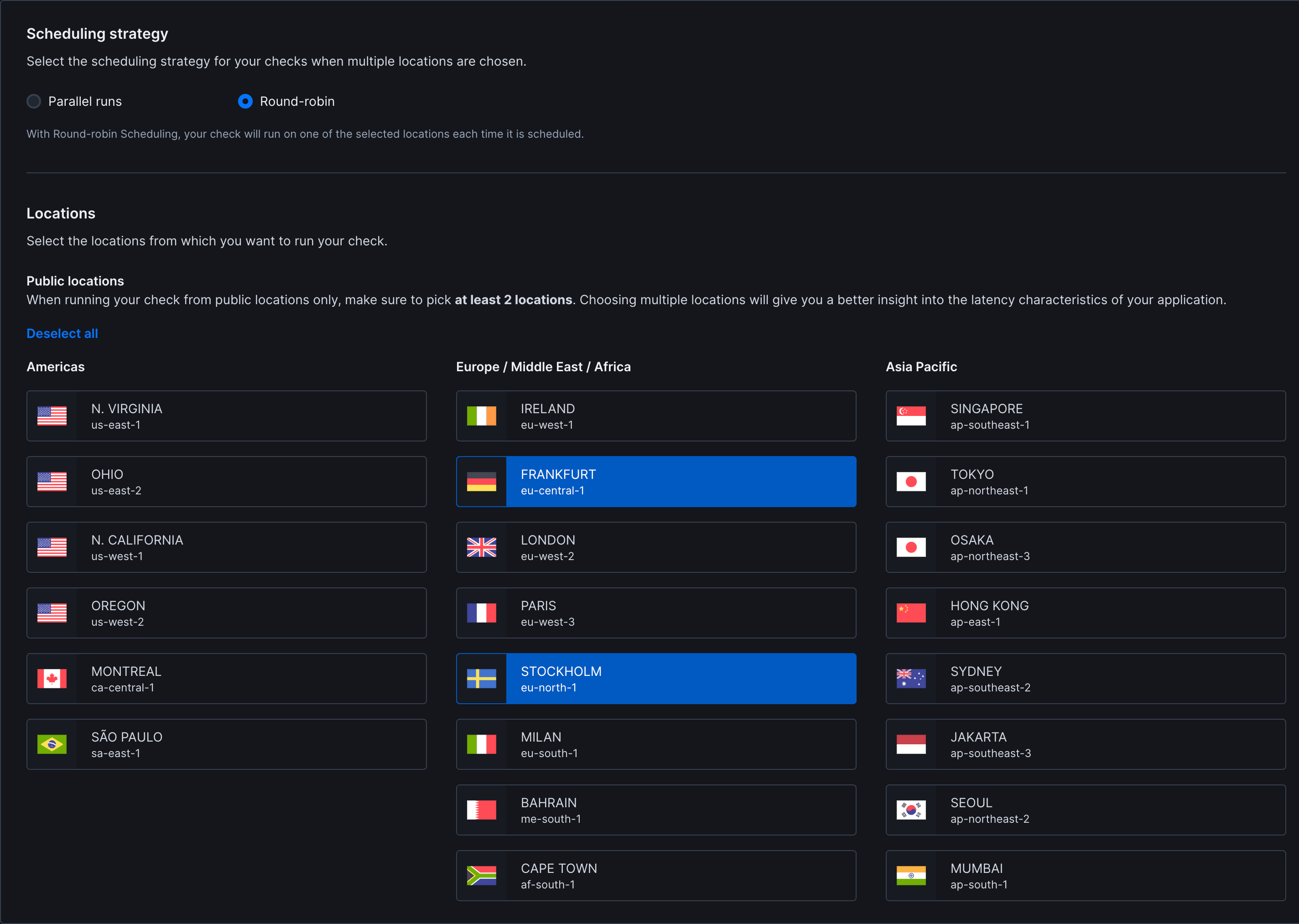
Basic Setup
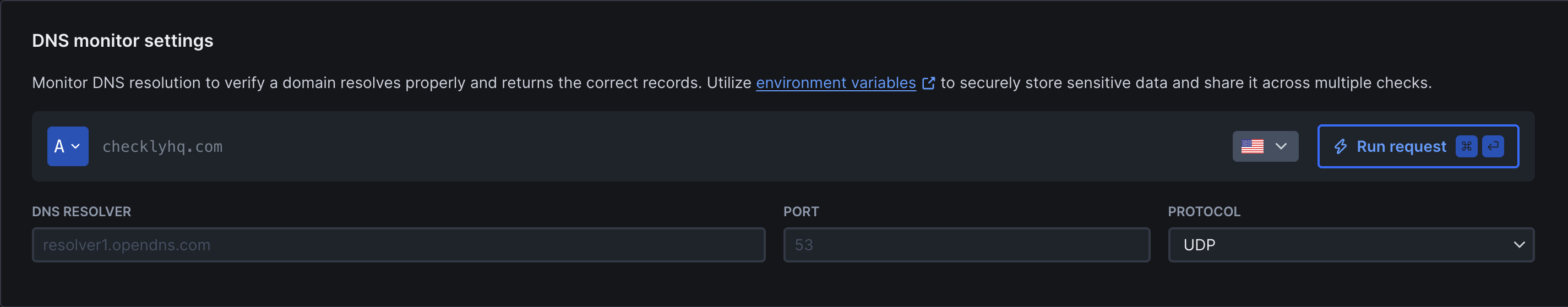
Specify the domain and record type you want to check: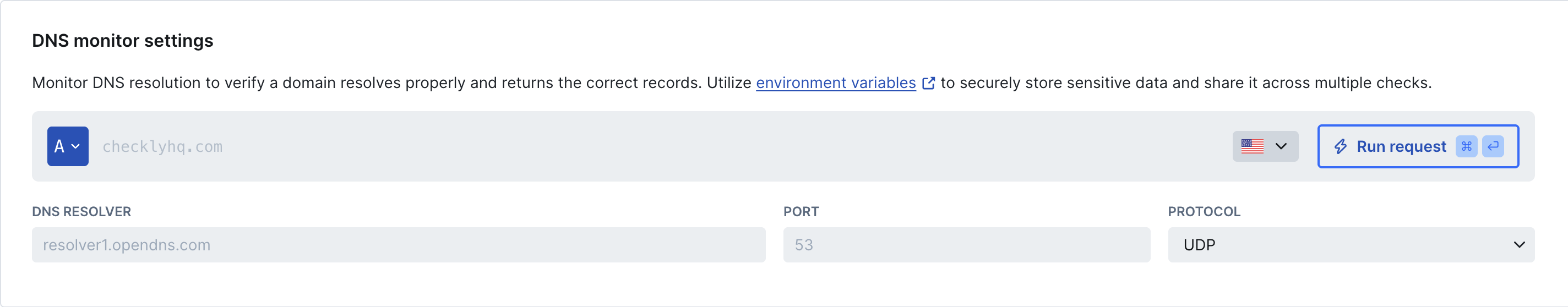
- Domain: The domain you want to monitor (e.g.
checklyhq.com) - Record type: The DNS record to query. See supported record types for the full list.
- DNS server: Queries use 8.8.8.8 (Google DNS) by default with automatic failover to 1.1.1.1 (Cloudflare) and an internal AWS resolver on errors. You can specify a custom nameserver and port (e.g.,
1.1.1.1:53ordns.google:53) to test resolver-specific behavior - Protocol: You can pin DNS queries to UDP-only or TCP-only.
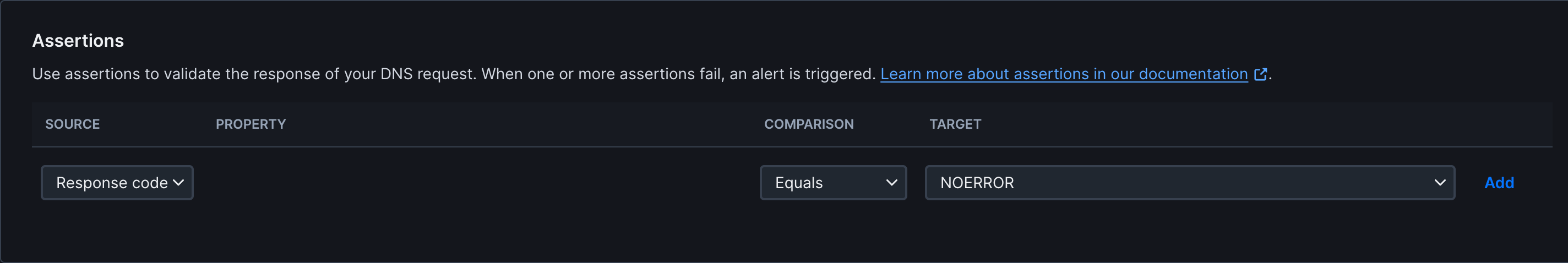
Assertions
Assertions let you define what the expected result of a DNS query should be. The raw and JSON responses are shown on the results page of a DNS monitor run and can be used as a reference when defining assertions.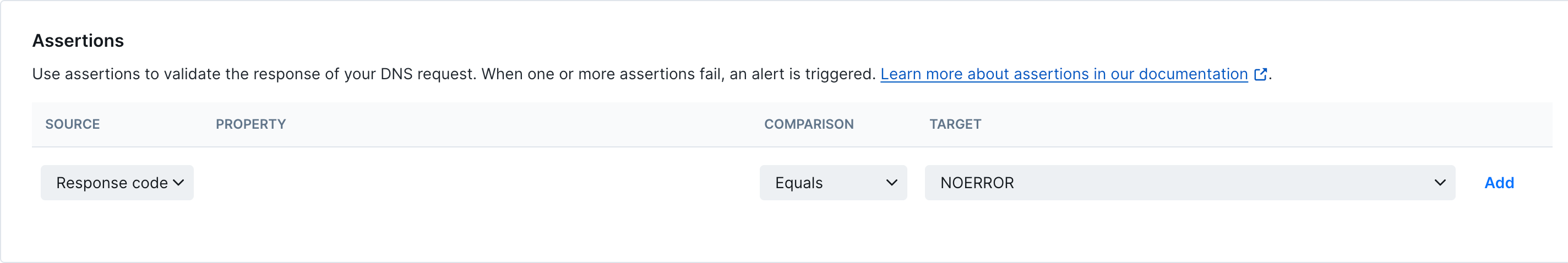
- Response time: The lookup time in milliseconds. Use this to set thresholds for failed lookups
- Return code: By default, DNS monitors pass when the return code is NOERROR and fail on error codes (FORMERR, SERVFAIL, NXDOMAIN, etc.). You can override this behavior by defining a custom return code assertion
- Text response: The raw DNS response as plain text. Use this to check for specific strings in the response
- JSON response: The DNS response parsed as JSON. This allows you to target specific fields using JSON path assertions. The response structure varies by record type. See JSON response schemas below for all supported record types.
$.Answer.length→ verify the number of records returned$.Answer[0].TTL→ validate TTL values are within expected ranges$.Answer[0].data→ check specific IP addresses or record values$.Status→ verify the DNS response status code
JSON Response Schemas
The DNS response is parsed into a structured JSON format. All responses share a common structure:Answer- Array of DNS records returnedQuestion- The DNS query that was madeStatus- Response status (NOERROR, NXDOMAIN, SERVFAIL, etc.)TC- Truncated flagRD- Recursion desired flagRA- Recursion available flagAD- Authenticated data flagCD- Checking disabled flag
A Record (IPv4)
A Record (IPv4)
$.Answer[0].data- Check specific IP address$.Answer.length- Verify number of A records$.Answer[0].TTL- Validate TTL value
AAAA Record (IPv6)
AAAA Record (IPv6)
$.Answer[0].data- Check IPv6 address$.Answer[0].TTL- Validate TTL value
CNAME Record
CNAME Record
$.Answer[0].data- Verify canonical name target
MX Record
MX Record
$.Answer[0].data- Check MX priority and mail server (format: “priority hostname”)$.Answer.length- Verify number of mail servers
TXT Record
TXT Record
$.Answer[0].data- Verify SPF, DKIM, or other TXT records- Text response contains
v=spf1- Check for SPF record
NS Record
NS Record
$.Answer.length- Verify number of nameservers$.Answer[0].data- Check specific nameserver
SOA Record
SOA Record
primary-ns responsible-email serial refresh retry expire minimumCommon assertions:$.Answer[0].data- Verify SOA record (contains serial number and nameserver)- Text response contains expected serial number
Record type support: DNS monitors currently support A, AAAA, CNAME, MX, NS, SOA, and TXT record types. Additional record types (SRV, CAA, PTR, etc.) may be added in future updates.
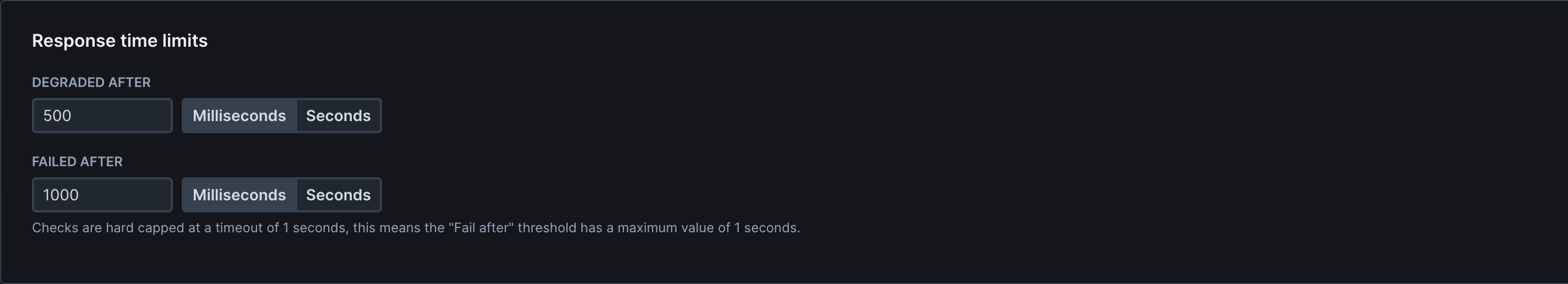
Response Time Limits
Define performance thresholds for degraded or failed states: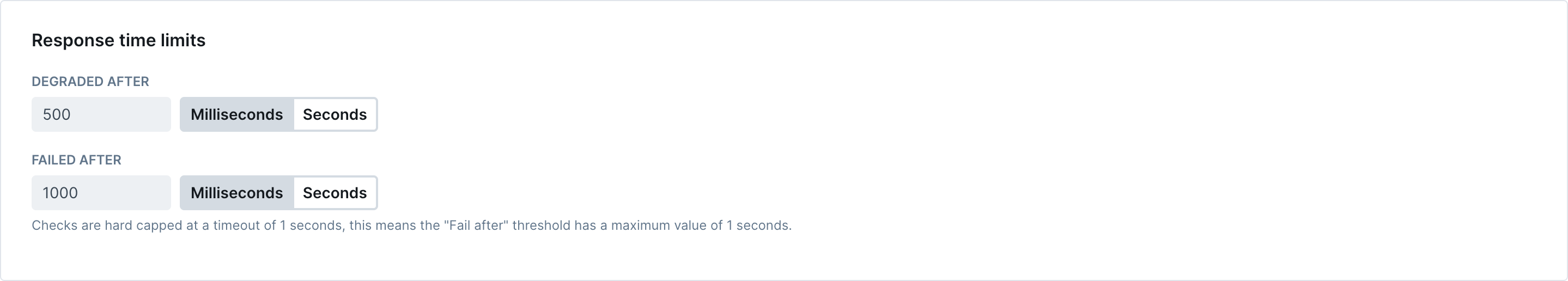
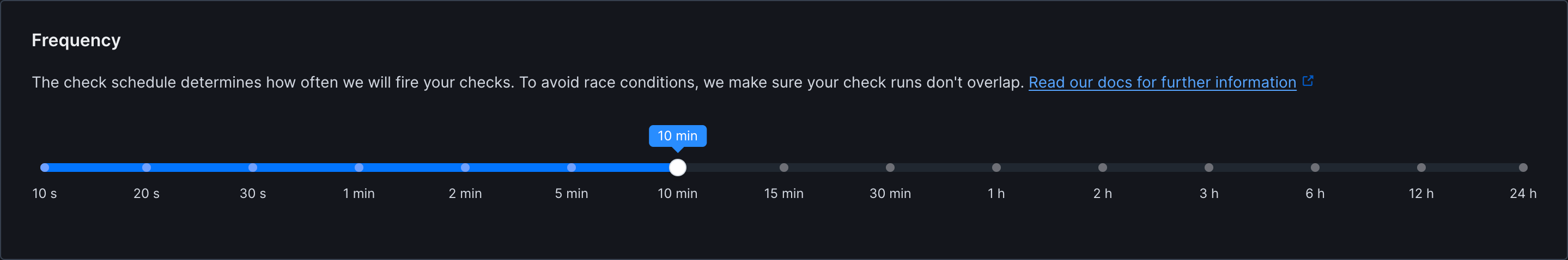
Frequency
Set how often the monitor runs (every 10 seconds to 24 hours):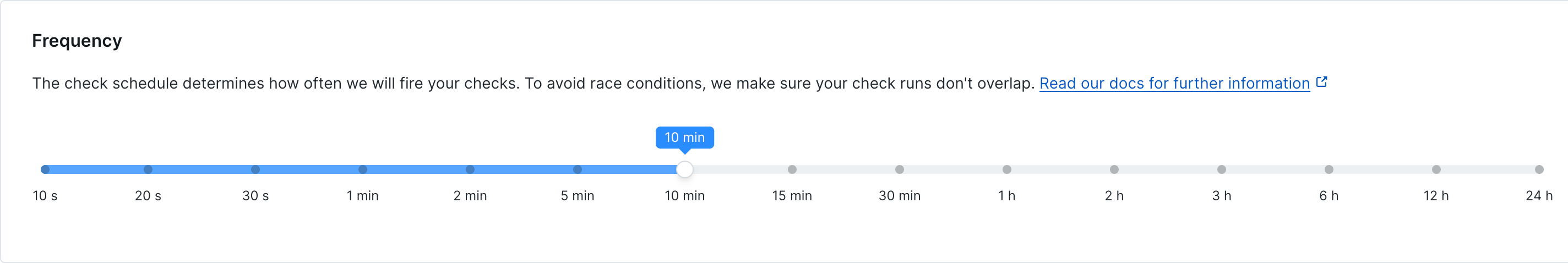
Scheduling & Locations
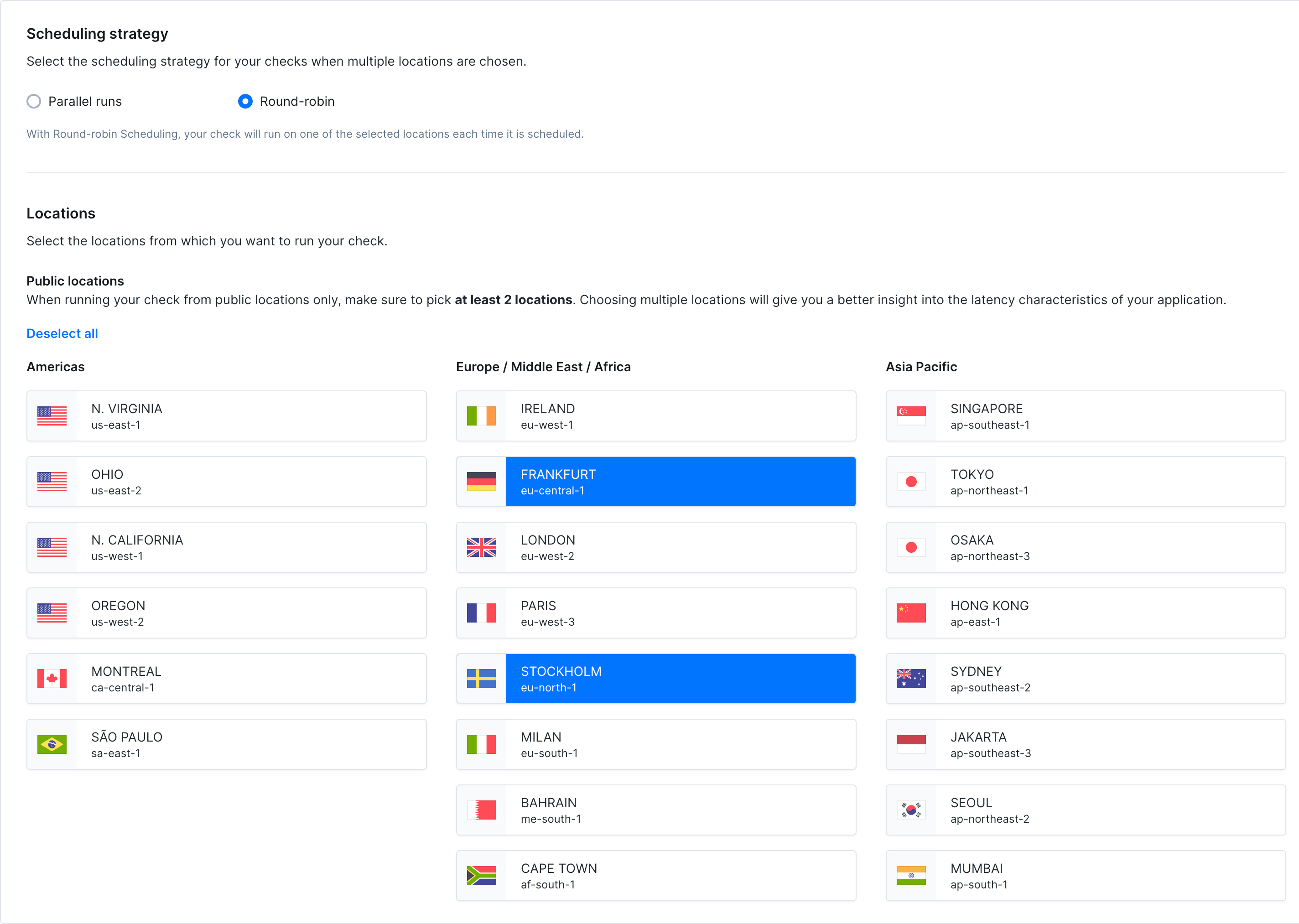
- Strategy: Choose between round-robin or parallel execution. Learn more about scheduling strategies
- Locations: Select one or more public locations to run the monitor from.
- Private locations: DNS monitors do not currently support private locations.
Additional Settings
- Name: Give your monitor a clear name to identify it in dashboards and alerts
- Tags: Use tags to organize monitors across dashboards and maintenance windows
- Retries: Define how failed runs should be retried. See retry strategies
- Alerting: Configure your alert settings, alert channels, or set up webhooks for custom integrations
Common Use Cases
Monitor CDN failover with multiple A records
Monitor CDN failover with multiple A records
Scenario: Your CDN provides multiple IP addresses for redundancy. You need to ensure all IPs are reachable.Configuration:
- Domain:
cdn.example.com - Record type: A
- Assertions:
$.Answer.lengthequals4(verify all IPs present)$.Answer[0].TTLis less than300(ensure low TTL for quick failover)$.Answer[0].dataequals expected IP address
Verify email security records (SPF, DKIM, DMARC)
Verify email security records (SPF, DKIM, DMARC)
Scenario: Monitor SPF, DKIM, and DMARC records to prevent email spoofing.Configuration:
- Domain:
example.com - Record type: TXT
- Assertions:
- Text response contains
v=spf1 $.Answer[0].datacontainsv=spf1
- Text response contains
- Domain:
_dmarc.example.com - Record type: TXT
- Assertions:
- Text response contains
v=DMARC1 $.Answer[0].datacontainsp=rejectorp=quarantine
- Text response contains
Monitor mail server configuration
Monitor mail server configuration
Scenario: Ensure primary and backup mail servers are correctly configured.Configuration:
- Domain:
example.com - Record type: MX
- Assertions:
$.Answer.lengthis greater than1(at least 2 MX records)$.Answer[0].datacontains10 mail.example.com.(priority 10 + hostname)- Text response contains
mail.example.com
Test DNS propagation after zone transfer
Test DNS propagation after zone transfer
Scenario: After updating nameservers, verify all nameservers return consistent results.Configuration:
- Domain:
example.com - Record type: NS
- Create separate monitors for each nameserver:
- Monitor 1: DNS server
ns1.example.com:53 - Monitor 2: DNS server
ns2.example.com:53
- Monitor 1: DNS server
- Assertions:
$.Answer.lengthequals expected count$.Answer[0].dataequalsns1.example.com.orns2.example.com.